Payment Transaction Authorization
Traditional transaction monitoring systems analyze only limited payment-related data.
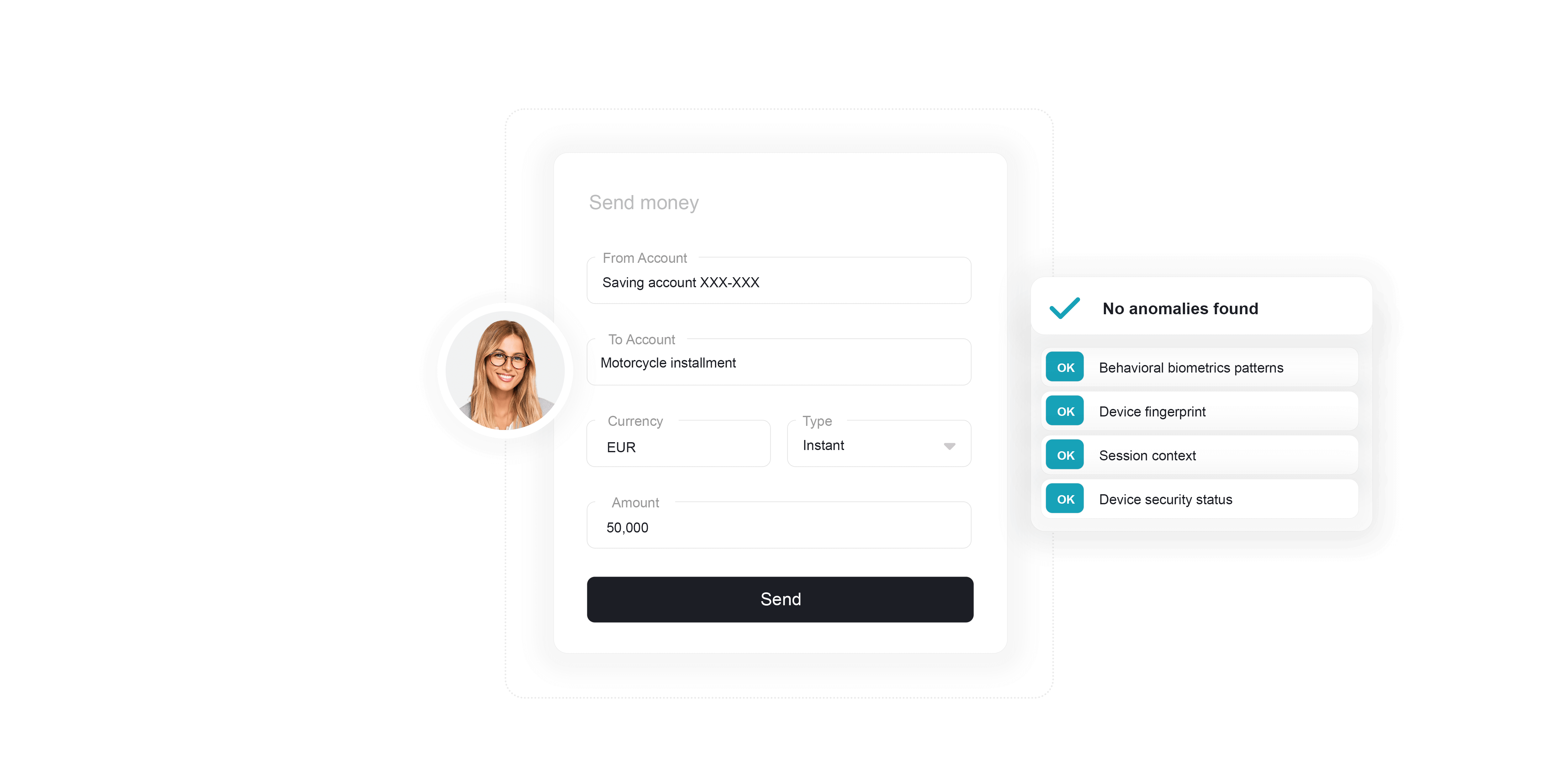
Leading to more false positives, even insignificant payments trigger alerts with these traditional systems as the payment-related data doesn’t align with the client’s spending patterns. ThreatMark offers a solution by providing detailed contextual information about the session, removing noise, and providing forensic-like data about every transaction to make the investigation most efficient.
Improve authorization
with contextual data.
Many transaction monitoring systems in use today focus solely on analyzing payment-related data. With numerous false positives from ineffective monitoring, the impact on bank staff to review these false results in heavy additional costs and time inefficiencies.
ThreatMark provides an additional layer of data that goes beyond payment-related data. Continuously verifying the user’s identity and intentions through behavioral biometrics, session parameters, transaction details, and other interactions across all digital channels, ThreatMark provids detailed information on user interactions and context by implementing deep behavior profiling.
This extensive dataset improves detection rates, soaring by 70%, while simultaneously slashing false positives by 90%.
Frequently Asked Questions
-
How does ThreatMark provide context for authorization?
ThreatMark’s Behavioral Intelligence Platform provides an additional layer of detailed information on user interactions and context by implementing deep behavior profiling. This consists of:
- Behavior biometrics (patterns in typing, mouse movements, touch events, and other interactions),
- Typical spending & login routines (unusual amounts, frequency, location, time) and
- Security checks (presence of financial malware, outdated browser, rooted phone).
-
What is continuous verification?
Continuous authentication is a security method that involves continuously verifying the identity of a user through behavioral biometrics throughout their session. Unlike traditional authentication methods, such as passwords or biometric scans performed only at the initial login, continuous authentication continuously monitors various user signals to ensure that the user remains authenticated and authorized.
-
Transactional Risk Analysis
To determine a low-level of risk, banks need to analyze various factors of a transaction in real time. ThreatMark provides a comprehensive solution that considers all necessary factors to avoid unnecessary MFA whenever possible.
Learn more
-
3D Secure Card Payments Authorization
E-commerce requires strong security measures like 3D Secure to prevent Card-Not-Present (CNP) fraud. 3DS adds an extra layer of security for online credit card transactions but can sometimes cause inconvenience and lead to high transaction abandonment.
Learn more
-
Strong & Invisible Authentication
Strong and invisible authentication crucially balances advanced security with a seamless customer experience. Utilizing technologies like behavioral biometrics and behavioral analytics, authenticating users subtly and effectively can minimize the risk of fraud and unauthorized access.
Learn more
Traditional fraud prevention tools are no longer enough.
Speak with a ThreatMark Fraud Fighter to find out more about our comprehensive approach to fraud disruption.