SIM Swap Scams & How to Prevent Them
SIM swap scams are one of the most damaging and high-profile scams in the modern era.
To be clear, SIM swap today may be also referred to as port-out scam, SIM splitting, simjacking and SIM swapping.
This article aims to further explore this scam and the methods of prevention. Accordingly, the article is divided into the following sections:
- Definition and SIM swap scam concept
- SIM swap scams impact and stats
- How to prevent SIM swap frauds
- Conclusion
SIM swap scam definition & concept
In SIM swap scams the attacker hijacks the victims’ phone number and assigns it to the SIM card owned by the fraudster.
The essence of the SIM swap scam is an impersonation or account takeover type of fraud which starts when the fraudster acquires the personal information of the victim.
Personal information can be obtained by various means, but usually, it includes some social engineering, phishing, or vishing attempts. They can be also bought on the (dark) web or even scraped from social media.
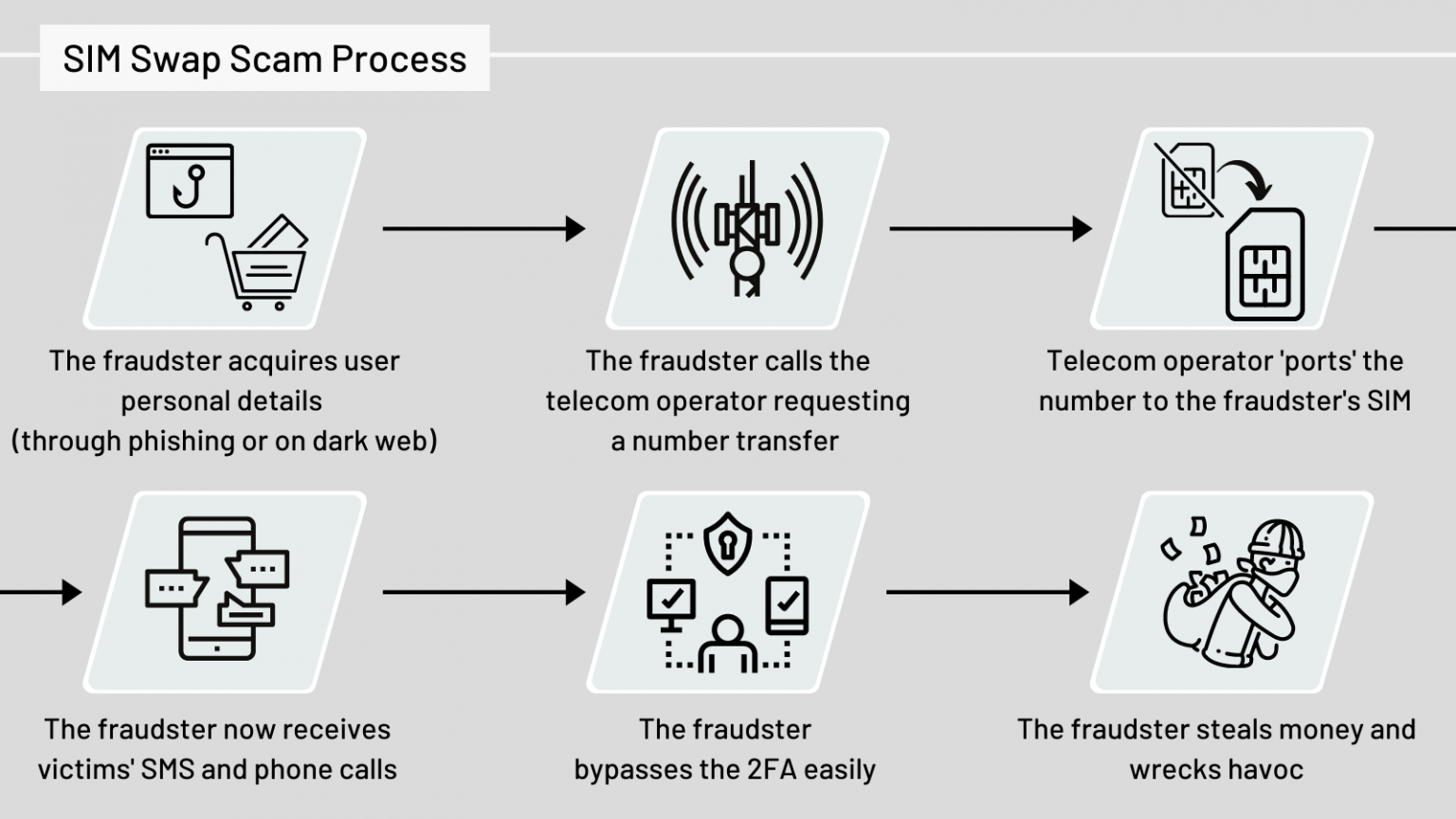
Once the fraudster has the relevant personal information, they’ll contact the victim’s telecom provider reporting a stolen or a lost phone. At this point, the fraudster impersonates the victim and persuades the telecom provider to transfer the victim’s phone number to the fraudster’s SIM card.
Usually, this transfer (a.k.a porting) feature is used when a telecom customer lost their phone or simply switching the providers or services. It’s a standard feature and procedure, but it is abused a lot by fraudsters.
Interestingly, there are also cases where telecom employees were bribed by the fraudsters to transfer the phone numbers to fraudster’s SIM cards. [1]
What happens when someone gets SIM Swapped?
Once the scam is done, the victims’ SIM card is disconnected and access to the phone number, incoming calls and SMSs are in the hands-on of the fraudsters.
This allows fraudsters to intercept all the communication that usually goes on the victim’s phones. Yes, from phone calls to SMS and OTPs (One Time Passwords) – with a successful SIM Swap – the fraudster has access to the victim’s most critical communication.
The only way the victim can know that something is awry is by seeing the phone being disconnected from the carrier and not receiving any phone calls, SMS, or data on the phone.
Though, in mid-march 2021, a new type of SIM swap type of scam which relies on SMS forwarding and redirection was discovered.[2] In this scenario the hacker abused a bulk SMS service for businesses, Sakari, to reroute the SMS to their number.
This scenario is troubling as the user doesn’t have any idea that something is wrong with the SIM card – the SMSs get redirected without the user being aware at all. The only thing the victim can notice – is the lack of received SMS. Which may not raise red flags at once.
SIM swapping and SMS redirects are particularly impactful these days as many secured and valuable services rely on SMS one-time passwords (OTPs) or phone calls as a second-factor authentication (2FA).
And it is these secured services – online banking, utilities, saving accounts… – which are usually the end goal of the scammers. With phone numbers in their hands, fraudsters can incur significant damages.
SIM swap scams stats & impact
One of the most famous SIM swap scams happened in 2019 when a hacker used the technique to gain access to Twitter’s CEO Jack Dorsey account.[3] Luckily no major damages were done or influenced by this attack but it shone the light on the severity of such scams.
Another often cited SIM swap attack occurred in the crypto arena. In 2018, a group of hackers scammed digital currency investor Michael Terpin (CEO of Transform Group) incurring damages of around $23.8 million with data stolen from smartphones by SIM swaps.[4] Although unsuccessfully, Mr. Terpin sued AT&T for $200 million in damages, claiming that AT&T allowed hackers to swap his SIM card through an elaborate scheme.[5]
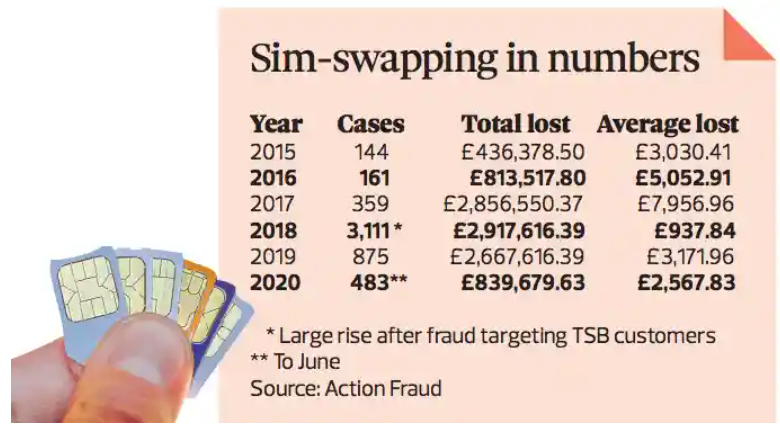
SIM swap attacks are gaining steam throughout the world. The sharp increase in incidents was noted by UK’s Action Fraud in June 2020 when they reported 483 cases, twice the number than in 2019, and 144 in 2015. [6]
In their 2019 IC3 Report, the FBI notes an example of a SIM swapping group leader arrest that led to the seizures of over $18 million, five vehicles, a $900,000 home, and hundreds of thousands of dollars in jewelry. The SIM swapping scheme had targeted hundreds of victims, compromised hundreds of cryptocurrency accounts, and caused approximately $40 million in losses.[7]
In March of 2020, Europol a group of hackers believed to have stolen over €3 million in a series of SIM swapping attacks.[8] The group struck over 100 times, stealing between €6,000 and €137,000 from bank accounts of unsuspecting victims per attack.[9]
The SIM swap attacks are very personal and can be impactful. Which.co.uk reported a story about Garth Pollard who was a victim of the SIM swapping attack where the attacker spent £13,000 over 48 hours.[10]
Surely such a case is not unique nor a solitary one.
So how to stay safe from SIM swap frauds?
How to prevent SIM swap scams
Since SIM swap attacks are personal, a great deal of protection lies on the end-user.
Fostering a great deal of awareness, privacy and skepticism is a great start for safety in the online world.
Furthermore, installing apps from trusted sources, clicking on verified and trusted links, not downloading files from unknown senders and keeping the data private are actionable guidelines and advice everyone should follow by default.
In their infographic Europol sums up what individuals can do to minimize the risk of being SIM swap scammed: [11]

The thing with SIM swapping is that sometimes – if the fraudster bought needed details elsewhere – it is invisible to the victim. This usually means that there will be considerable damage done before the victims notice something is awry.
And this is where businesses should do more to protect their user’s assets and data.
This is where – for the banks and financial industries – ThreatMark comes into play.
How ThreatMark prevents SIM swap fraud
ThreatMark is a complete fraud prevention solution safeguarding online digital experiences across all digital channels.
Our advanced technology uses various approaches and data analyses to understand subtle differences in user behavior – thus precisely knowing who the real user is and who is the fraudster.
And this differentiation is crucial in SIM swap frauds and any other frauds with account takeover intentions.
In essence, only telecoms and users can stop SIM swap as it happens.
But with ThreatMark, banks and financial institutions have a solution to stop the fraudster from abusing the stolen account.
Meaning that even if the SIM swap happens – the fraudster can’t do anything with it. They can’t steal money nor do anything with the stolen identity due to ThreatMark’s deep behavioral profiling and 3-layered fraud prevention.
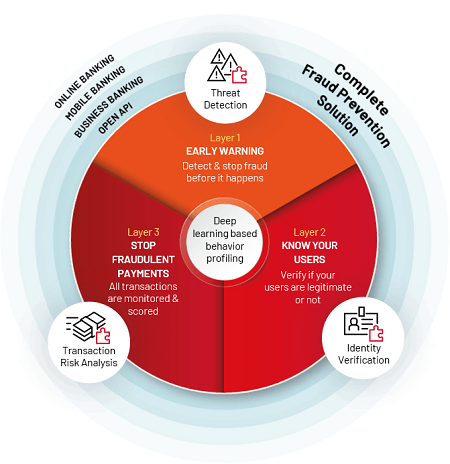
For banks and financial institutions our technology provides 3-layer protection against such scams:
- Layer 1 – Early threat detection. ThreatMark’s technology detects diverse types of threats, malware, phishing, BOT detection, RAT (Remote Access Trojan) – the fraudster can use to steal users’ credentials, accounts and commit fraud.
- Layer 2 – User identity verification – in this layer ThreatMark focuses on understanding the user-specific data. From the device, session to behavioral biometrics – ThreatMark uses these data points to build a completely trusted user profile. This deep behavioral profiling enables businesses to precisely identify any anomalies from the verified, trusted profile. Thus, stopping fraudsters, imposters from doing any damage even if they have taken over the account.
- Layer 3 – Transaction Risk Analysis – in this final layer ThreatMark focuses on transactions and payments behavior data. It is here again where ThreatMark can help detect any anomalies from legitimate user payments and behavior and those from the fraudster.
More details on ThreatMark AFS (Anti Fraud Suite) features, layers and scope, here.
Combining all these 3 layers is one powerful solution – that provides precise knowledge on the legitimate user behavior – giving banks a way to stop SIM swap fraud in the roots.
The fraudsters can steal thousands of credentials and swap thousands of SIM cards – but they can’t hack nor copy the real user behavior or hundreds of other nuanced data points our technology looks at.
Conclusion
SIM swap scam is an impersonation or account takeover type of fraud that starts when the fraudster acquires the personal information of the victim.
It is a relatively simple fraud attempt with devastating effects. SIM swap is problematic as businesses are using SMS or calls as a 2nd factor authentication that provides great privileges. Additionally, it takes some time for victims to figure out that they’ve been scammed, and their blocked SIMs include a nefarious activity.
There’s a lot the users can do to prevent being victims of the SIM swap, and conversely, account takeover scams. Being mindful, critical and skeptical about online data, shady links and calls – helps.
Businesses on the other hand could do much more. They should understand how their users can be a victim of SIM swap scams and secure their services accordingly.
For banks and financial institutions, ThreatMark provides everything they need to fight fraud across digital channels, including SIM swap and other account takeover scams.
[1] Vice, AT&T Contractors and a Verizon Employee Charged With Helping SIM Swapping Criminal Ring, https://www.vice.com/en/article/d3n3am/att-and-verizon-employees-charged-sim-swapping-criminal-ring [last accessed: 15.04.2021]
[2] Vice, A Hacker Got All My Texts for $16, https://www.vice.com/en/article/y3g8wb/hacker-got-my-texts-16-dollars-sakari-netnumber [last accessed: 15.04.2021]
[3] CNBC, Here’s how the recent Twitter attacks probably happened and why they’re becoming more common, https://www.cnbc.com/2019/09/06/hack-of-jack-dorseys-twitter-account-highlights-sim-swapping-threat.html [last accessed: 15.04.2021]
[4] Reuters, U.S. cryptocurrency investor sues suburban NYC teen for $71.4 million over alleged swindle, https://www.reuters.com/article/us-crypto-currency-lawsuit-idUSKBN22J32V [last accessed: 15.04.2021]
[5] Bitcoin.com, Judge Dismisses $200M Damages Claim in SIM-Swap Crypto Lawsuit Against AT&T, https://news.bitcoin.com/judge-dismisses-200m-damages-claim-in-sim-swap-crypto-lawsuit-against-att [last accessed: 15.04.2021]
[
6] The Guardian, Sim-swap fraud is on the rise. How can you stop it happening to you?, https://www.theguardian.com/money/2020/sep/13/sim-swap-is-on-the-rise-how-can-you-stop-it-happening-to-you [last accessed: 15.04.2021]
[7] The FBI, 2019 Internet Crime Report, https://www.ic3.gov/Media/PDF/AnnualReport/2019_IC3Report.pdf [last accessed: 15.04.2021]
[8] Europol, the sim highjackers: how criminals are stealing millions by highjacking phone numbers, https://www.europol.europa.eu/newsroom/news/sim-highjackers-how-criminals-are-stealing-millions-highjacking-phone-numbers [last accessed: 15.04.2021]
[9] Ibid.
[10]Which.co.uk, Sim-swap fraud: how criminals hijack your number to get into your bank accounts, https://www.which.co.uk/news/2020/04/sim-swap-fraud-how-criminals-hijack-your-number-to-get-into-your-bank-accounts/ [last accessed: 15.04.2021]
[11] Europol, ibid.