
Loan Fraud
In loan fraud, or lending fraud, fraudsters typically deceive financial institutions or individuals to obtain loans through false pretenses, fake documentation, or identity theft. This results in financial losses for the lender, and often impacts the creditworthiness of innocent victims. Fraudsters use stolen identities or create synthetic identities to evade revealing their true IDs to apply for credit without intending to repay the loan or the debt accrued on a credit card.
TALK TO A FRAUD FIGHTER
The scale of the problem.
-
4.3%of all applications have fraudulent intent.
-
91,000reports of application fraud in 2021 in the UK.
-
85%of financial institutions experience account opening fraud.
Recognize and stop lending fraud as it happens.
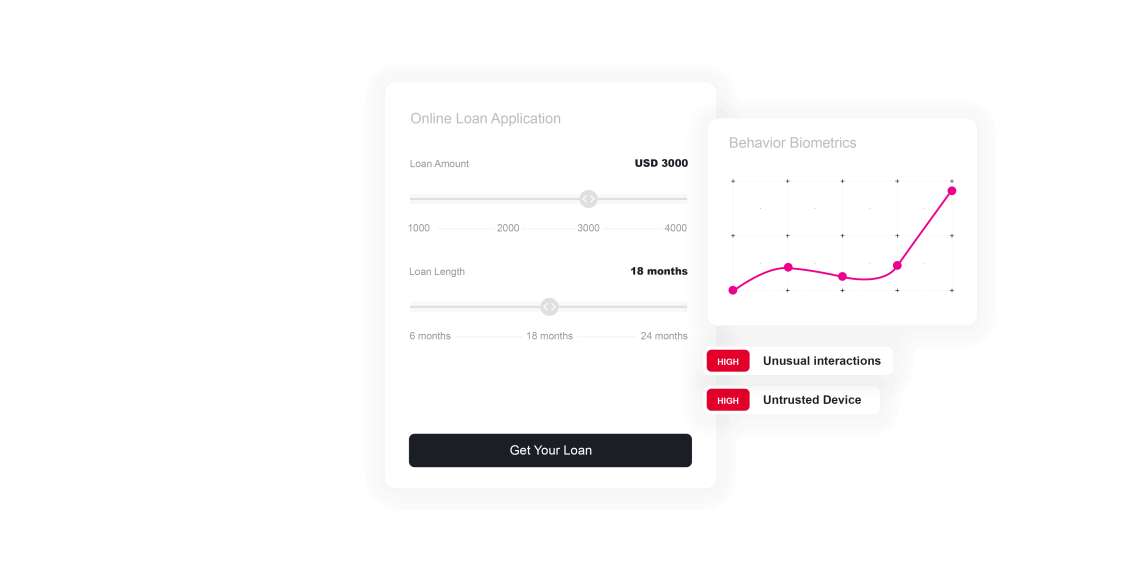
ThreatMark identifies discrepancies that suggest fraudulent activity by analyzing application patterns and applicant behaviors. It can flag inconsistencies in application data, unusual speed in filling out forms, or atypical patterns in navigating the loan application process, which are common in fraudulent applications. The platform can detect and alert to the use of stolen or synthetic identities by comparing application details with known patterns associated with legitimate borrowers, enabling institutions to scrutinize suspicious applications more closely before approving loans, thereby reducing the risk of fraudulent disbursements.
ThreatMark’s behavioral intelligence enhances the institution’s ability to balance security with customer experience. By accurately distinguishing between genuine and fraudulent loan applications, financial institutions can maintain efficient and user-friendly processes for legitimate borrowers while implementing additional verification steps only where necessary. This targeted approach helps maintain trust in the institution’s lending services without burdening honest customers.

Mitigating lending fraud.
-
Device Intelligence
Device Intelligence uses an exhausting set of different device features and context information extracted from the browser, device OS, hardware properties of different device subsystems, network information, and other data sources to identify the physical device accurately. ThreatMark employs deep behavioral profiling to tell whether the currently visiting devices are associated with legitimate users or fraudsters or have never been seen before.
-
Behavioral Intelligence
ThreatMark Platform captures the exact details of the user's interaction with the interface of an application and analyzes the person's cognitive and behavioral traits. Using primary data the ThreatMark Platform collects during user activity, it employs state-of-the-art machine learning methods to identify historically observed legitimate and criminal behavior patterns.
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.