FluBot Malware – All You Need to Know & to Act Now
FluBot is a newly discovered Android banking malware family whose presence has been increasingly worrying in the past months.
Although it uses many of the tricks found in older malware families, this malware family has made a lot of progress in just a handful of months, infecting many devices, spreading quickly and inflicting serious damage.
The malware targets different mobile apps based on the device’s language setting. So far, there have been detections of the malware targeting banking apps mainly in Spain, but evidence suggests it may move on to other markets, such as Poland, Germany, Hungary and the UK.
Besides targeting mobile banking apps, FluBot has its sights on cryptocurrency-related mobile apps as well; regardless of the device’s language setting.
FluBot Malware Infection Cycle
The FluBot Malware Infection usually follows this pattern:
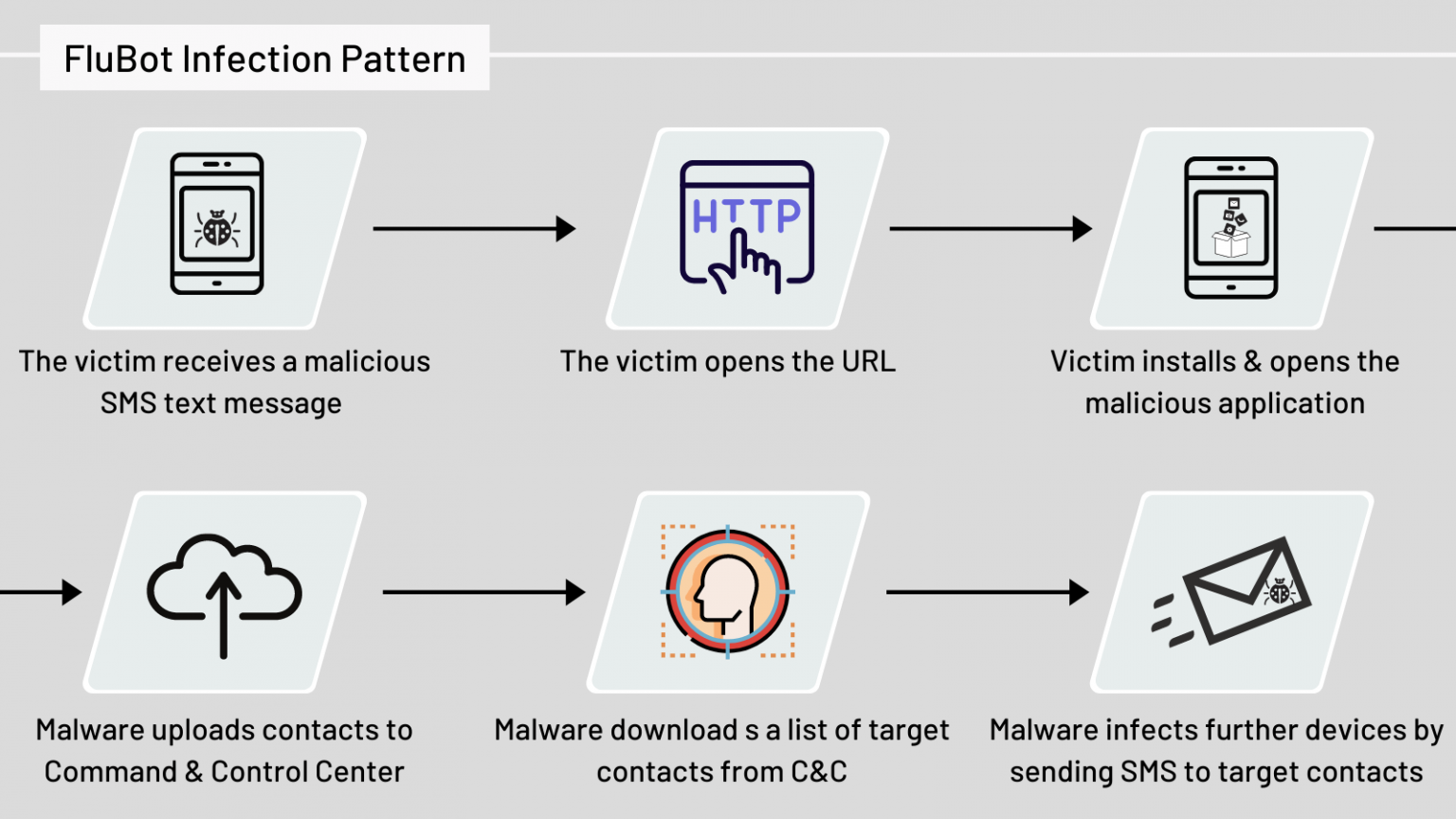
* (C&C = command and control server)
- The victim receives a text message informing them about the delivery of a package.
- The message contains a link to a website containing the malware, disguised as the delivery company’s application. The malware has used the DHL, UPS and FedEx brands.
- The victim downloads and installs the application.
- The malware uploads the victim’s contacts to its C&C (Command & Control) server.
- The C&C server sends a list of phone numbers to the victim’s device.
- The victim’s device sends text messages to these numbers, which are other potential victims. To prevent detection, the victim’s device only sends text messages to numbers, not in their phone book. Additionally, the malware adds the contacted numbers to the phone’s blacklist – in that way, there is no way to alert the “spreading” device of its behavior by a recipient of the text message.
C&C – Domain Generation Algorithm (DGA)
Once the malware application has been installed and opened, it asks the victim to enable its accompanying accessibility service.
After the rights are granted, the malware grants itself several permissions by abusing the accessibility service and starts trying to connect to a C&C server.
Interestingly, there is no server or domain name hardcoded in the application, the malware dynamically generates domain names which it then attempts to resolve.
It may take a few tries until it manages to find a resolvable domain name, after which the real communication begins.

One of the earlier samples trying to connect to a C&C server using generated domain names
C&C – DNS over HTTPS – CloudFlare, AliDNS, Google Public DNS
Based on our research the FluBot evolves quickly. The current samples use DNS over HTTPS (DoH) to resolve the generated domain names.
This is likely done to make it harder to detect the malware – the malware contacts legitimate domains (cloudflare-dns.com, dns.alidns.com, dns.google) and resolves the domain name using those services.
Once it manages to resolve one of the generated domain names, communication with the C&C server begins.
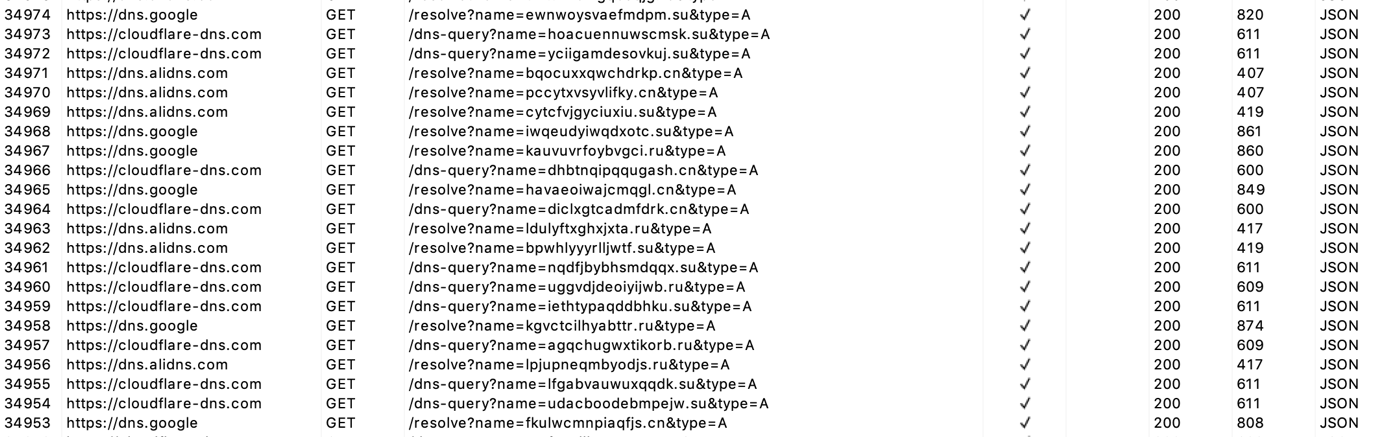
The first evolution of the FluBot malware only used CloudFlare’s DoH service for domain name resolution. Newer samples are using multiple services as seen in the screenshot above.
Injecting on top of the apps
After establishing a connection to the attacker’s server, the malware sends a list of installed applications to the server.
Then, the C&C responds with a list of applications it wants to target. This leads the malware to retrieve injects which are then shown on top of the targeted applications.
In the end, this results in the victim unknowingly entering their credentials into this spoofed overlaid view.
The video above shows the injection happening on top of the BankInter application.
The image gallery below shows other examples of the injects targeting other applications.
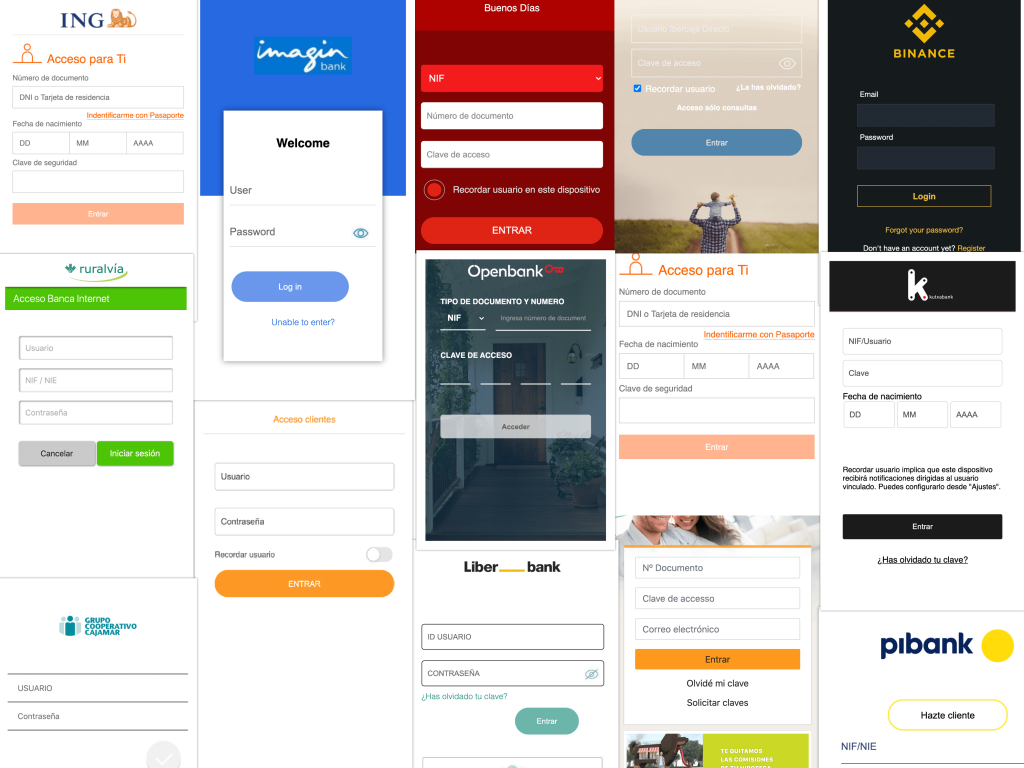
In our investigation we discovered the following banking injects:
"Bankinter" - com.bankinter.launcher
"BBVA" - com.bbva.bbvacontigo
"Cajasur"- com.cajasur.android
"Grupo Cooperativo Cajamar' - com.grupocajamar.wefferent
"Imagin Bank" - com.imaginbank.app
"Kutxabank" - com.kutxabank.android
"Ruralvia" - com.rsi
"Laboral" - com.tecnocom.cajalaboral
"Banco Santander" - es.bancosantander.apps
"Bankia" - es.cm.android
"Evo Banco" - es.evobanco.bancamovil
"IberCaja" - es.ibercaja.ibercajaapp
"Liber Bank" - es.liberbank.cajasturapp
"Openbank" - es.openbank.mobile
"Pibank" - es.pibank.customers
"Unicaja Banco" - es.univia.unicajamovil
"ING" - www.ingdirect.nativeframeAnd two related to cryptocurrency trading platforms:
"Binance" - com.binance.dev
"Coinbase" - com.coinbase.andriodOther FluBot Malware functionality
FluBot malware possesses the ability to perform other harmful actions on the victim’s device, including:
- Disabling the Play Protect mechanism
- Reading, intercepting & sending text messages
- Reading the list of contacts
- Adding phone numbers to the device’s blacklist
- Uninstalling applications
- Blocking notifications
- Stealing credit card information
Arguably all these are very powerful in the wrong hands and can be very damaging for the victims and their well-being.
And how does one get rid of FluBot?
How to get rid of FluBot
When the victim tries to uninstall the malware from their device, the malware actively protects itself against that by closing the settings app whenever the user tries to uninstall it. As seen in the video below:
Though, luckily there are several ways how you can uninstall the malware despite this protection.
- Use Android’s safe boot
- Hold down the Power button.
- Long tap on the Restart option – a prompt will appear; confirm you want to reboot into safe mode.
- Go into the system settings, find the malware app among the installed applications and uninstall it.
- Use adb – this is a bit more advanced, as you need to connect your device to a PC and issue commands to it through the command line. You can follow this guide to uninstall the malware this way.
Recently, another way of uninstalling the infected has appeared – an analyst created an Android application. This application uninstalls the FluBot application from your phone.
However, recent instances of the FluBot malware are defending against this easy way of uninstalling the app (again showcasing the rapid pace of development of this malware).
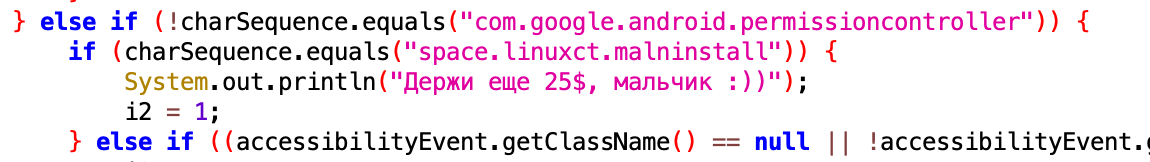
The code that detects the uninstaller – the uninstaller’s package name is space.linuxct.malninstall
How does ThreatMark protect against this malware?
ThreatMark’s SOC team is constantly on the lookout for the latest threats in the digital world. Their mission is to discover threats such is FluBot, dissect and learn the modus operandi.
Once the details are discovered the SOC team updates the Threat Intelligence of our ThreatMark Anti Fraud Suite.
Onward all our clients receive detections and alerts on any signs of infection and overlay inject. This intelligence further allows our clients to block any fraudulent transactions, or other activities, coming from the infected devices.
To learn more about how ThreatMark detects the FluBot malware, and other threats, contact us.
Conclusion
Mobile malware is an ever-evolving threat that requires constant monitoring. With quickly evolving malware variants, such as FluBot, it’s important to have an up-to-date database of threats at your disposal to be able to effectively protect your users against becoming the victims of these attacks.
Companies can invest in advanced technological solutions – like ThreatMark’s AFS – that help in the process of detecting, preventing, and mitigating mobile malware attacks before they inflict any damage.


