9 Highly Effective Methods that Innovative Companies Use IT Software
Cybersecurity is serious. Whether you own a web-based infrastructure, online account, or a website, you can be a victim of a cyberattack. Even banking applications you have installed on your devices can be a ticking bomb if unprotected.
People nowadays take advantage of the Internet to promote and sell products in different ways, reach their customers, and perform financial transactions. Unfortunately, cybercriminals and hackers also use the Internet as a mechanism to spread malware and conduct cyberattacks.
The increasing prominence of blockchain technology, for instance, is making smart contracts that enable the conflict-free exchange of virtual currencies prone to bugs. We’ve seen this in 2016 when a hacker made off over $50m of cryptocurrency by injecting a bug in smart contract code and another similar attack worth $30m in 2017. This smart contract software guide is essential for getting a good grasp of what this digital, self-executing contract is for.
According to the 2019 Official Annual Cybercrime Report (ACR), organizations fall for ransomware attacks every 14 seconds. This means that cybercrime has already taken place somewhere as you read the first three paragraphs of this article up to this point.
While we only generally hear about cybercrimes against government sites, banks, and large companies, cybercriminals also target small businesses. They are amongst the prime targets as they are often deemed lacking resources, least protected, and thereby easy to penetrate.
What is IT security software?
IT security software is also known as cybersecurity software. It is an essential tool in ensuring the security and privacy of business from cyberattacks, identity theft, and unauthorized data access. It protects the application, the network and the IT system as a whole.
Cybersecurity technologies are important for all types of businesses, especially when you think about how essential your digital systems and the Internet are for daily operations.
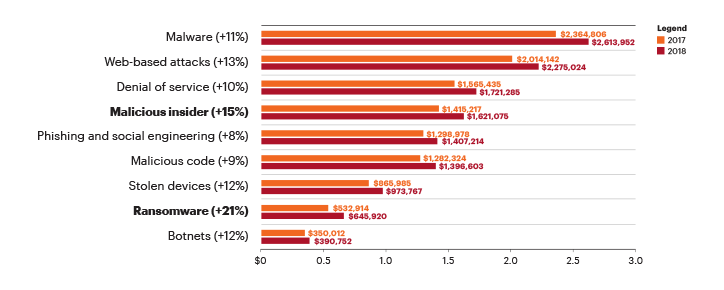
Cybersecurity software list includes application security, information security, network security, disaster recovery, operational security, and so forth. They need constant updates for various types of cyber threats like ransomware, malware, social engineering, and phishing.
Cybercrime is a global phenomenon that we can’t simply ignore. IT security software can be quite costly, but it is a worthwhile investment. The amount is no match to the probable cost when your business fall victim to cybercrime. According to Accenture’s 2019 Global Cost of Cybercrime Study, the average cost of cybercrime for an organization grew 12% to $13.0M in 2018 from a year ago. Over the last five years, the cost has grown 72% or $5.5 million on average. The financial service is the most targeted industry with the average cost reaching as much as$18.5 million in 2018.
Below are 9 ways highly innovative companies use IT software.
1. Verify user identity with behavioral biometrics
More advanced functions include verification of user identity based on behavioral biometrics. This is the preferred choice of companies that understood the need to constantly verify the user identity without penalizing the User Experience. By having a tool that performs deep behavioral profiling in the background, you can ensure strong authentication security without disrupting the end-user. With this, innovative companies can fight online fraud by distinguishing legitimate users from fraudsters and avoiding legal issues and financial loss in the long run.
2. Use cybersecurity software for hybrid technology deployments
Businesses are no longer confined in a four-wall setting. Staff members access data from everywhere at any time. As such, a security system that enables cloud user access has to be in place. It needs to be flexible enough allowing multiple deployment options and must be manageable in supporting the mobility of the modern workforce. Companies tend to run security applications at corporate headquarters while they opt for cloud-based security proxy solutions to support mobile workers and remote offices. Security monitoring software can provide this hybrid support throughout security controls using a central management dashboard.
3. Decide a mix of in-house cybersecurity solutions and outsourced managed service options
Due to the shortage of cybersecurity skills, companies select which cybersecurity solutions they will outsource to managed security service providers and those they will run in-house. Best cybersecurity software enables seamless interoperability with central command-and-control of product and managed service combinations.
4. Integrate cybersecurity solutions with Application Program Interfaces (APIs)
No cybersecurity solution can provide comprehensive security coverage. Thus, companies usually choose platforms that have considerable openness to ecosystem partners, developer support, and API third party integration for automation. This also encourages networking among the cybersecurity software users where they are provided with a platform to share development best practices.
5. Utilize cloud-based backend services
Intelligence and data are king and must be shared across customers. Imagine the cloud as the backend brain of IT security software. Cloud-based services will generate malicious behaviors across all the customers and software users together, run them through sophisticated machine learning algorithms, track new threat intelligence, and offer customized threat intelligence curation and customized analytics for a customer’s specific systems, applications, network, and so forth.
Organizations and individual users share input and obtain intelligence from the community. A good platform also intake external intelligence to provide more security to the community
6. Integrate cloud-based workloads, servers, networks, and endpoint protection together.
Everything needs to be secured regardless of location. Whatever left unprotected would become your weakest link. Most enterprises today come with balkanized cybersecurity tools that are mutually hostile to one another. Innovative companies, meanwhile, integrate these tools to cover their IT infrastructure and function altogether as security forces.
7. Perform aggregate threat detection, prevention, and response
Any IT manager would tell you that they want cybersecurity solutions with at least 95% efficacy in detecting attacks. They set their IT cybersecurity software to track malicious behaviors throughout the kill chain, run aggregated alerts that combine all the anomalous breadcrumbs together, and offer functions to dismiss processes, quarantine applications, or restore configurations to a recognized trusted mode.
Cybersecurity software must be adaptive, where continuous improvement of preventive security controls are made through response, detection, and intelligence.
8. Provide an aggregated alternative to individual cybersecurity management
A critical feature of cybersecurity solutions is that it enables central control across all products and services. That entails policy and configuration management, along with reporting and general administration. Cybersecurity tools enable businesses to operate all essential parts of cybersecurity in a single dashboard, including malware sandboxing management, network security management, endpoint security management, and so forth. This ensures visibility and control of the most common threat vectors.
9. Apply anti-malware filters to primary threat vectors
This is an obvious application of IT security software. Studies have shown that about 90% of cyber attacks stem from weaponized URLs, malicious attachments, or phishing emails. Other threat vectors are cloud, endpoint, and humans. Decent cybersecurity software comes with filter and monitoring tools to common threat vectors to block malware and provide visibility into malicious, suspicious and unusual behaviors. Others also feature intrusion and anti-virus systems to protect businesses against data leakages by keeping track of data transfers and confidential files.
It Security Software Is Definitely One of the Key Areas Your Company Should Invest In
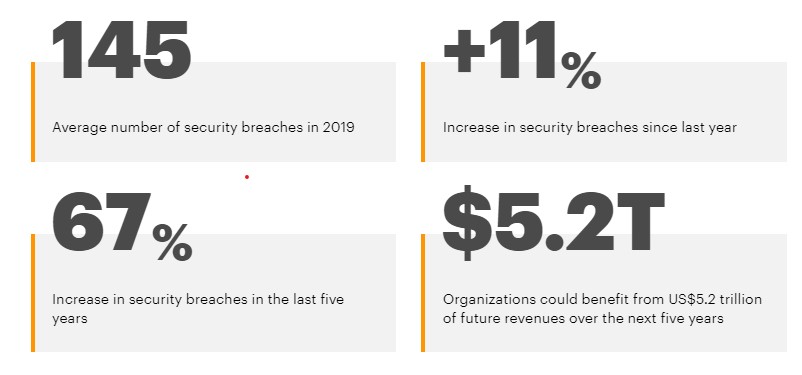
Several fraudulent cyberattacks like fraudulent malware driven attacks and social-engineering attacks have affected many businesses and forced several to cease operations. Cybersecurity has become more crucial to businesses of all sizes amidst the growing sophistication of security breaches and cyberattacks. Accenture study has shown that improved cybersecurity protection could reduce cybercrime costs and beef up revenues. It estimated that the total value at risk worldwide is around $5.2 trillion over the next five years.
Cyber threats are evolving with new tactics and new variants. More advanced cyberattacks are emerging with new intentions, victims, and technologies. The surge of Malware-as-a-Service and Ransomware-as-a-Service enables anybody, regardless of his technical skills, to carry out a cyberattack with ease.
Greater awareness of cyberattacks and the damages it can bring has driven organizations of all sizes to improve their cybersecurity measures. Facebook Messenger revamped for business use is a good example after the social media giant suffered backlash on how they handle data and privacy.
On the other hand, this is also motivating cybercriminals to stage more sophisticated cyberattacks. Extensive security risks, quicker and more advanced attacks all make it very taxing for IT managers to avert the threats. The Accenture study also mentioned that almost 8 in 10 business leaders say new business models are also introducing technology vulnerabilities faster than they can be secured. Hence, there must be a reliable cybersecurity system in place to prevent attacks from incurring substantial damages.
Investing in a decent IT security software is a must. You can build trust among your customers if you can prove that your business is adequately protected from all forms of cyber threats. They will have more confidence in availing of your products or services. Check out a security software list and decide which you think is best for your IT system.